Coding Challenge #6: Environment Variable Manager
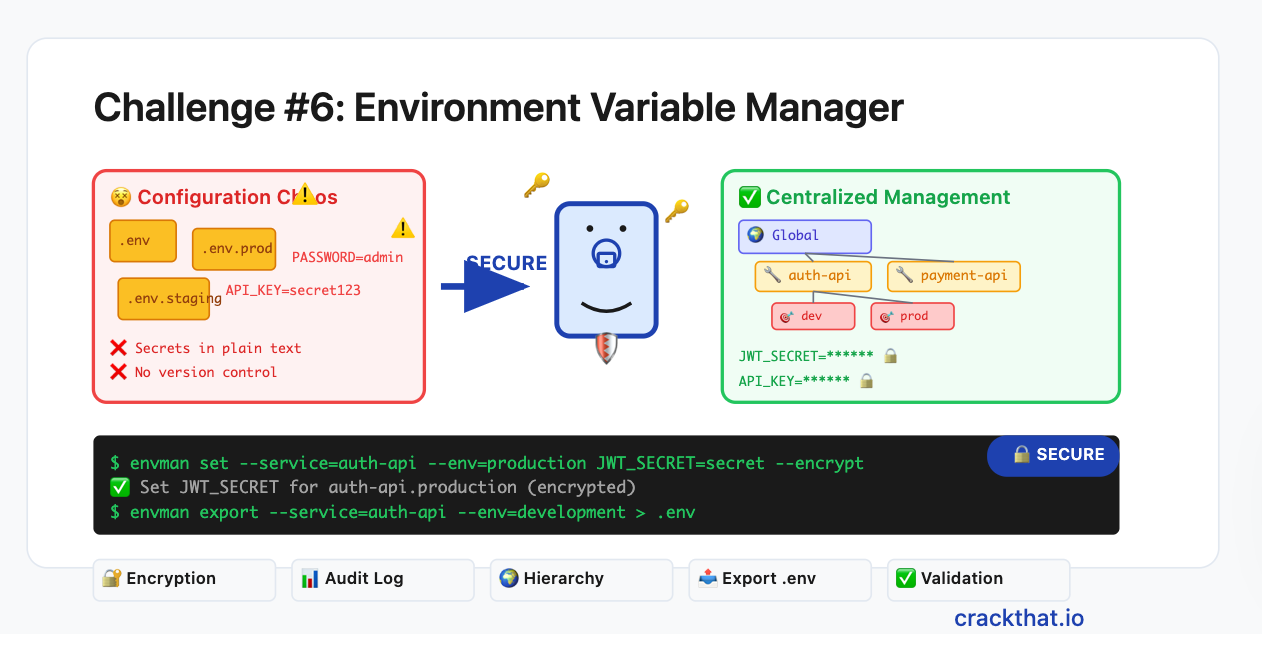
Your team is managing 15 microservices across development, staging, and production environments. Each service needs different environment variables: database URLs, API keys, feature flags, and configuration settings. Developers are constantly asking "What's the database URL for staging?" or "Which API key should I use for the payment service?"
You're tired of maintaining scattered .env files, Slack messages with credentials, and the security nightmare of API keys in plain text. You need a centralized tool to manage environment variables securely across different environments and services.
Your Mission
Build an environment variable management tool that stores, retrieves, and manages configuration data for multiple services and environments with proper security practices.
Requirements
Your tool must:
Store environment variables for multiple services and environments
Support hierarchical configuration (global → service → environment overrides)
Encrypt sensitive values (passwords, API keys) at rest
Provide commands to set, get, list, and delete variables
Export environment files (.env format) for local development
Support variable templates and substitution
Validate required variables for each service/environment
Include audit logging for all changes
Support importing from existing .env files
Sample Usage
# Set global variables (shared across all services)
envman set --global DATABASE_HOST=db.company.com
envman set --global LOG_LEVEL=INFO
# Set service-specific variables
envman set --service=auth-api DATABASE_NAME=auth_db
envman set --service=auth-api JWT_SECRET=super-secret-key --encrypt
# Set environment-specific overrides
envman set --service=auth-api --env=production DATABASE_HOST=prod-db.company.com
envman set --service=auth-api --env=development DATABASE_HOST=localhost
# List variables for a service/environment
envman list --service=auth-api --env=development
# Export .env file for local development
envman export --service=auth-api --env=development > .env
# Import from existing .env file
envman import --service=payment-api --env=staging < payment.env
# Validate required variables
envman validate --service=auth-api --env=production
Expected Output
Environment Variable Manager
============================
📋 Listing variables for: auth-api (development)
================================================
🌍 Global Variables:
-------------------
DATABASE_HOST=db.company.com
LOG_LEVEL=INFO
🔧 Service Variables (auth-api):
-------------------------------
DATABASE_NAME=auth_db
JWT_SECRET=****** (encrypted)
PORT=3000
REDIS_URL=redis://localhost:6379
🎯 Environment Overrides (development):
---------------------------------------
DATABASE_HOST=localhost (overrides global)
DEBUG=true
📊 Summary:
-----------
Total variables: 6
Encrypted values: 1
Overrides: 1
💾 Export .env format:
----------------------
DATABASE_HOST=localhost
LOG_LEVEL=INFO
DATABASE_NAME=auth_db
JWT_SECRET=decrypted-secret-here
PORT=3000
REDIS_URL=redis://localhost:6379
DEBUG=true
✅ All required variables present for development environment
Sample Data Structure
{
"global": {
"DATABASE_HOST": "db.company.com",
"LOG_LEVEL": "INFO",
"COMPANY_NAME": "TechCorp"
},
"services": {
"auth-api": {
"variables": {
"DATABASE_NAME": "auth_db",
"JWT_SECRET": {
"value": "encrypted:AES256:base64encodeddata",
"encrypted": true
},
"PORT": "3000"
},
"environments": {
"development": {
"DATABASE_HOST": "localhost",
"DEBUG": "true"
},
"production": {
"DATABASE_HOST": "prod-db.company.com",
"DEBUG": "false",
"JWT_SECRET": {
"value": "encrypted:AES256:differentprodkey",
"encrypted": true
}
}
},
"required": ["DATABASE_HOST", "DATABASE_NAME", "JWT_SECRET", "PORT"]
},
"payment-api": {
"variables": {
"STRIPE_KEY": {
"value": "encrypted:AES256:stripekey",
"encrypted": true
},
"WEBHOOK_SECRET": {
"value": "encrypted:AES256:webhooksecret",
"encrypted": true
}
},
"required": ["STRIPE_KEY", "WEBHOOK_SECRET", "DATABASE_HOST"]
}
},
"audit_log": [
{
"timestamp": "2025-07-19T10:30:00Z",
"action": "SET",
"service": "auth-api",
"environment": "production",
"variable": "JWT_SECRET",
"user": "alice@company.com"
}
]
}